New Capabilities Help Enterprises Visualize Attack Paths, Enforce MFA on Unmanaged Local Accounts, and Align Identity Security With the Zero Trust Framework
- The identity risk exposure management feature adds identity threat detection capabilities that help uncover how attackers could escalate privileges or move laterally within the environment
- With local user MFA, enterprises can extend enterprise-grade MFA to previously unmanaged local accounts
Read about AD360’s identity risk exposure management at https://mnge.it/riskexposuremgmt and local user MFA capabilities at https://mnge.it/local-user-mfa
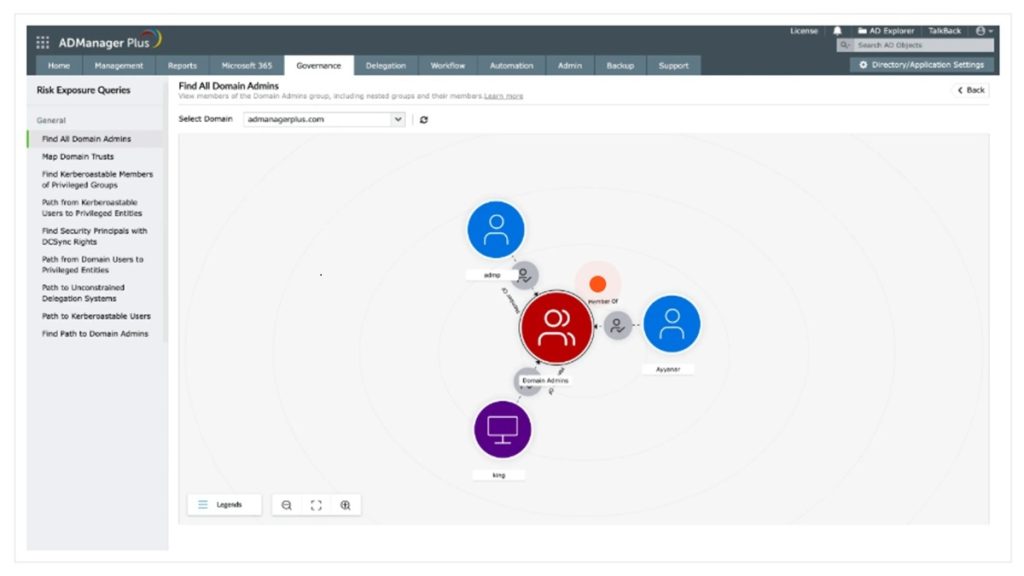
ManageEngine, the enterprise IT management division of Zoho Corporation, today announced the general availability of two major security capabilities in AD360 — its converged identity and access management (IAM) platform: Identity Risk Exposure Management and Local User Multi-Factor Authentication (MFA). The release is designed to help security and IT teams detect and close privilege-escalation attack paths and to harden unmanaged local accounts — two identity vectors attackers continue to exploit at scale.
Identity remains the primary entry point for modern attacks. Citing industry telemetry, the Verizon 2025 Data Breach Investigations Report found credential abuse was the initial access vector in 22% of breaches and highlighted the recurring exploitation of poorly managed local accounts and privilege paths across thousands of confirmed incidents. ManageEngine’s latest AD360 update moves identity from a passive access layer to an active security control that surfaces risk and prevents exploitation in real time.
“With this release, ManageEngine AD360 moves beyond traditional IAM by embedding identity threat defenses into core identity operations,” said Manikandan Thangaraj, vice president of ManageEngine. “By turning identity data into actionable security insights, we’re helping customers make IAM the first line of defense, not a check box.”
What’s new — capabilities and how they work

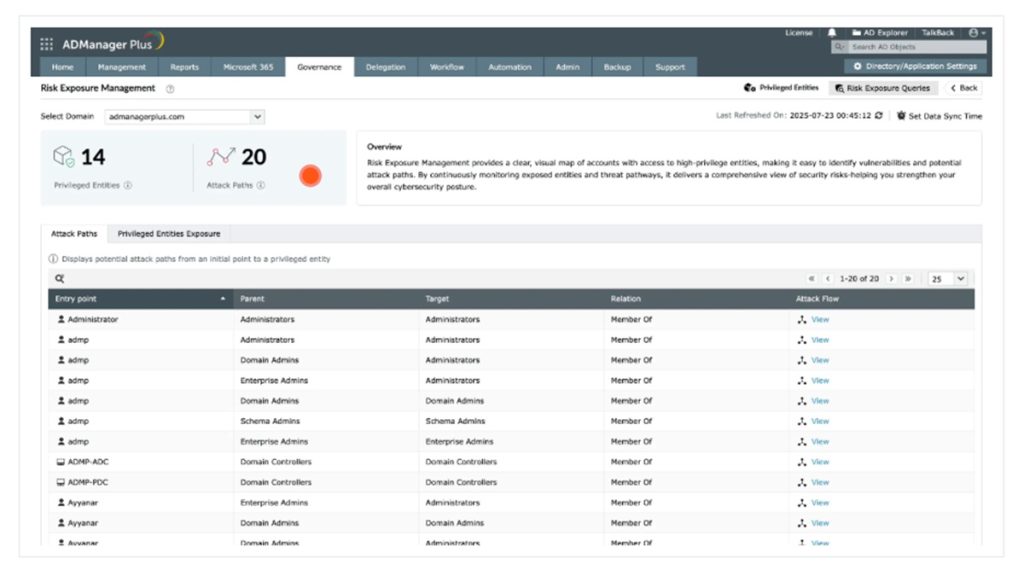
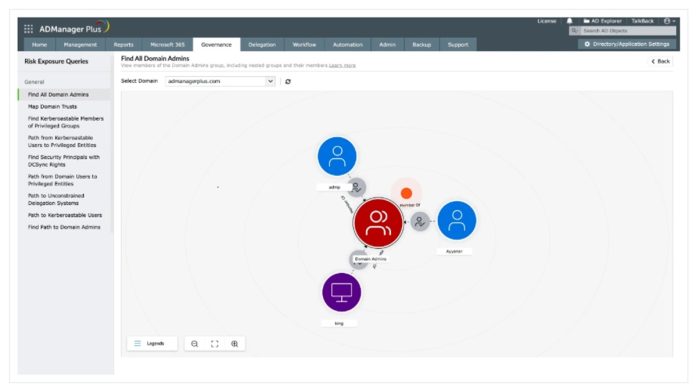
Identity risk exposure management (graph-based attack-path analysis)
- AD360 now builds a live graph model of Active Directory where objects (users, groups, computers) are represented as nodes and inheritance/permission relationships are edges.
- The graph engine automatically detects lateral-movement corridors and multi-step privilege escalation chains that adversaries can abuse.
- Risky configurations are prioritized by exposure level and potential impact, and the system provides concrete remediation guidance — for example: remove group nesting, remove legacy admin privileges, or apply conditional access controls.
- Alerts and dashboards help security teams visualize attack paths, investigate “who can reach what” in minutes, and verify fixes.
Local user MFA for non-domain and edge assets
- Extends adaptive MFA protections to local accounts on non-domain-joined servers, DMZ systems, test and lab assets — environments often excluded from centralized IAM yet targeted for persistence.
- Reduces the success of credential stuffing, replay attacks, and lateral-movement persistence by requiring an additional authentication factor before local sessions or privileged actions.
- Configurable policies allow organizations to enforce step-up authentication based on risk, asset profile, or user role.
ML-driven access recommendations
- Machine learning analyzes historical permission patterns and provisioning activity to suggest least-privilege changes during onboarding and access-review campaigns.
- Recommendations can streamline access certification by flagging anomalous entitlements and suggesting safe permission reductions.
Enhanced access certification & risk monitoring
- Expanded entitlement discovery now covers deeper object types and cross-checks Microsoft 365 roles and permissions alongside Active Directory context.
- New risk indicators and richer reporting improve continuous monitoring and simplify evidence collection for audits.
Why this matters — practical benefits
- Reduce attack surface: By revealing hidden privilege chains and risky local accounts, AD360 helps prevent common exploitation techniques used in initial access and persistence.
- Faster, prioritized remediation: Actionable remediation steps reduce the time between detection and mitigation, cutting dwell time.
- Stronger coverage for non-domain assets: Local-user MFA addresses a frequent blind spot — servers and appliances that aren’t joined to AD but still house privileged accounts.
- Operationally useful automation: ML recommendations and automated graph analysis reduce the manual effort of entitlement reviews and access clean-ups.
- Compliance & governance alignment: The new features help organizations strengthen controls related to Zero Trust (NIST SP 800-207) and meet specific requirements such as PCI DSS v4.0 (Req. 8), while simplifying evidence collection for SOX, HIPAA, and GDPR programs.
Typical use cases
- Security operations: SOC teams can investigate and visualize attack paths during incident response to understand potential lateral movement.
- IAM & AD administrators: Proactively identify and close privilege escalation paths as part of routine hygiene and hardening.
- Compliance teams: Run comprehensive certification campaigns with automated recommendations and audit-ready reports.
- Managed service providers (MSPs): Rapidly assess client AD risk posture and apply consistent local-MFA policies for hybrid environments.
Integration & deployment
AD360’s new capabilities are designed to work alongside existing Microsoft environments — combining Active Directory and Microsoft 365 telemetry to produce a unified identity risk picture. Local-user MFA integrates with on-premises and edge systems to provide additional assurance where domain controls are not present. Administrators can tune detection sensitivity, policy thresholds, and remediation workflows to match organizational risk appetite and operational processes.
Availability & next steps
The identity risk exposure management and local user MFA capabilities are generally available in AD360. Organizations interested in evaluating these features should contact ManageEngine for product demonstrations, implementation guidance, and pilot programs. AD360 continues to evolve with more analytics and automation planned to further narrow identity-centric attack surfaces.
For detailed product information, demos, or to discuss deployment scenarios, visit ManageEngine’s AD360 product pages or reach out to ManageEngine sales and technical teams for next steps.






![Samsung x Globe At Home: Your Gateway to a Smarter, Better Life [KV] Samsung and Globe AT HOME](https://www.wazzup.ph/wp-content/uploads/2026/02/KV-Samsung-and-Globe-AT-HOME-218x150.jpg)



